Cisco Umbrella¶
Cisco Umbrella protects enterprises by categorizing domains and providing feedback on whether or not a website is malicious.
- Recommended Method: Amazon S3 Bucket
Data Types¶
- UMBRELLA_DNS
- UMBRELLA_WEBPROXY
- UMBRELLA_FIREWALL
- UMBRELLA_IP
- CISCO_UMBRELLA_AUDIT
Caveats / Known Limitations¶
- Cyderes recommends the customer host the S3 bucket instead of the vendor so that Cyderes can setup an SQS notifications.
Configuration¶
Reference: https://docs.umbrella.com/deployment-umbrella/docs/cisco-managed-s3-bucket
- Follow the directions in the reference article
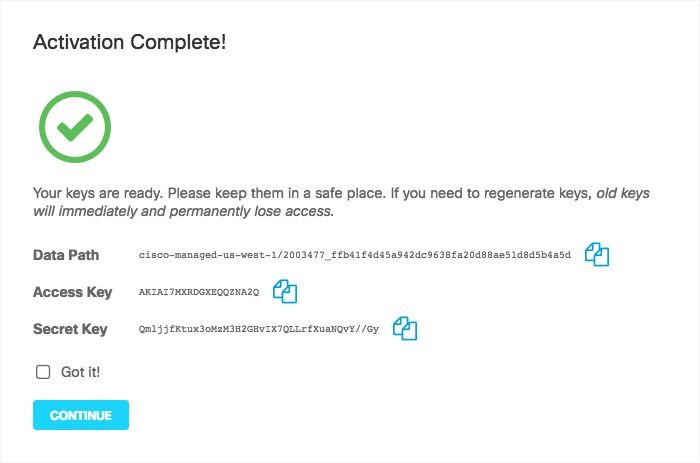
-
Next, follow these steps to create a Feed in Google SecOps and enable ingestion of Cisco Umbrella logs from the newly created bucket:
-
Navigate to SIEM Settings > Feeds.
- Click Add New Feed.
- On the following page, select Configure a single feed.
- From the Source type dropdown, choose Amazon S3.
- In the Log type dropdown, choose the appropriate log type based on the path you want to ingest logs from, such as Cisco Umbrella DNS or Cisco Umbrella Web Proxy.
- Click Next.
- Using your AWS S3 server access configuration, enter the required input parameters:
- Region
- S3 URI
- Source deletion option
- Select AWS access key and secret
- Access key ID
- Secret access key
- Click Next, then click Submit to complete the setup.