Windows DNS¶
DNS is a rich telemetry source that can help detect a wide array of attacks that would normally be very difficult to identify.
Data Types¶
- WINDOWS_DNS
File-based DNS Debug Logging¶
File-based DNS debug logging is the only way to monitor DNS events on Windows Server versions prior to 2012 R2. This is also a preferred way to ingest DNS events using NXLog Community edition that also has a high parse rate based on Chronicle’s default parsers. To import data using file-based logging, it MUST be enabled first.
DNS Debug Logging Configuration¶
To enable DNS Debug Logging, perform the following actions.
- Open the DNS Management console (dnsmgmt.msc)
- Right-click on the DNS Server and choose Properties from the context menu
- Under the Debug Logging tab, enable Log packets for debugging
- Mark the check boxes corresponding to the data that should be logged
- Set the File path and name to the desired log file location (be sure to use a location on the C: drive for the debug log path). Cyderes recommends something like: C:\Server\dns.log
- Ensure that NXLog has permissions to read from this path
- Restart DNS service
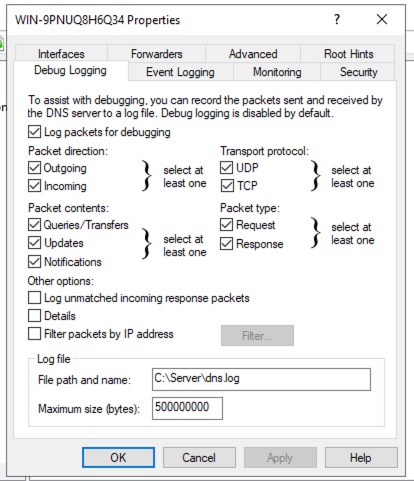
WARNING | DO NOT ENABLE DETAILS! This module does not support parsing of logs from DNS Debug Logging generated with the Details option enabled, as this will produce multi-line logs!
Additional Configuration of NXLog Configuration File¶
The NXLog config file’s DNS input section may also be modified based on the location of this log file path and name if C:\Server\dns.log is not used.
<Input dns>
Module im_file
File "C:\\Server\\dns.log"
SavePos TRUE
InputType LineBased
Exec if ($raw_event =~ /^#/) OR ($raw_event == '') drop();\
else\
{\
$Message = $raw_event;\
$SourceName = "DNS";\
}
</Input>
DNS Analytics Through Windows Event Logs¶
The Windows Event Log (im_msvistalog) module is primarily used to ingest DNS Server Audit Logs. It is also possible to configure the Windows Event Log module to read DNS Analytical logs. When performance is a concern, it is recommended to use NXLog Enterprise Edition for its ability to ingest through the Event Tracing for Windows (ETW) module.
DNS Audit logs are enabled by default on Windows Server 2012 R2 and later, and diagnostic logging should already be installed on Windows Server 2016 Technical Preview or later. To install and enable DNS diagnostic logging on Windows Server 2012 R2, first install the hotfix available at https://support.microsoft.com/kb/2956577.
DNS Analytics Configuration¶
- Type eventvwr.msc at an elevated command prompt and press ENTER to open Event Viewer
- In Event Viewer, navigate to Applications and Services Logs\Microsoft\Windows\DNS-Server
- Right-click DNS-Server, point to View, and click Show Analytic and Debug Logs. The Analytical log will be displayed.
- Right-click Analytical and then click Properties
- Under When maximum event log size is reached choose Archive the log when full, do not overwrite events
- Select the Enable logging checkbox and click OK when asked if log should be enabled
- Click OK again to enable the DNS Server Analytic event log
- By default, analytic logs are written to the file: "%SystemRoot%\System32\Winevt\Logs\Microsoft-Windows-DNSServer%4Analytical.etl". NOTE: Cyderes recommends moving logs to a different location, such as C:\Server\Microsoft-Windows-DNSServer%4Analytical.etl to avoid account permission issues with the System32 directory
Recommendation - NXLog Enterprise Edition¶
Cyderes recommends using NXLog Enterprise Edition installed on the primary Windows DNS servers in the environment. Generally, these are the DNS servers that are assigned as primary and secondary resolvers in the network properties of every PC. The objective in capturing this data is to gather the client which requested a domain and what the domain was resolved to. If the DNS request is forwarded on, the original client information is replaced by the forwarding source, so it is important to capture DNS from each point which could get the initial client DNS request if possible.
NXLog Enterprise Edition contains a feature to read the ETW providers, one of which contains all of the analytical logging information from Windows DNS. NXLog will consume events from that provider and send the data as syslog. Example NXLog configuration:
define ROOT C:\Program Files (x86)\nxlog
define OUTPUT_DESTINATION_ADDRESS <hostname>
define OUTPUT_DESTINATION_PORT <port>
Moduledir %ROOT%\modules
CacheDir %ROOT%\data
Pidfile %ROOT%\data\nxlog.pid
SpoolDir %ROOT%\data
LogFile %ROOT%\data\nxlog.log
<Extension syslog>
Module xm_syslog
</Extension>
<Input etw_dns>
Module im_etw
Provider Microsoft-Windows-DNSServer
</Input>
<Output out_dns>
Module om_tcp
Host %OUTPUT_DESTINATION_ADDRESS%
Port %DNS_DESTINATION_PORT%
Exec $EventTime = integer($EventTime) / 1000000;
Exec $EventReceivedTime = integer($EventReceivedTime) / 1000000;
Exec to_syslog_ietf();
</Output>
<Route 1>
Path etw_dns => out_dns
</Route>